Cyber security domain always talks about lack of skilled resources and tooling. We decided not to whine but rather help with the cause.
At Cyfinoid, open source is how we put this into action. Some projects are developed by our research team, while others come directly from our interns, who build complete tools during their paid internships.
This page is the central hub for all our open-source work. Each project is clearly attributed, so credit goes where it belongs.

GHNavigator is a client-side browser-based tool designed to simplify exploring GitHub repositories and analyzing Personal Access Tokens (PATs). It works entirely in your browser without requiring any server dependencies, ensuring tokens never leave your session.
Key Capabilities
-
Repository Browser: Navigate through repositories with an intuitive interface, view file structures, and group repos by organization.
-
Token Analyzer: Validate token scopes, perform repo enumeration, and run bulk token checks securely.
Who Can Benefit
-
Security Teams: Validate PATs and map repository access safely.
-
Developers & DevOps: Manage and test tokens with clear visibility into their scope.
-
Bug Bounty Hunters: Investigate and validate leaked tokens without risking exposure.
-
Researchers: Explore repository structures and API behaviors efficiently.
Getting Started
👉 Try it live: GHNavigator GitHub PagesAlternative Option
-
Clone the repository:
-
Open
index.htmlin your browser. -
Enter a GitHub token and begin exploring.
Security Considerations
-
Tokens remain in your browser session only.
-
No backend servers or tracking involved.
-
Built with GitHub REST API v3 best practices.
| Categories : |
Software Supply Chain Security
|
|---|

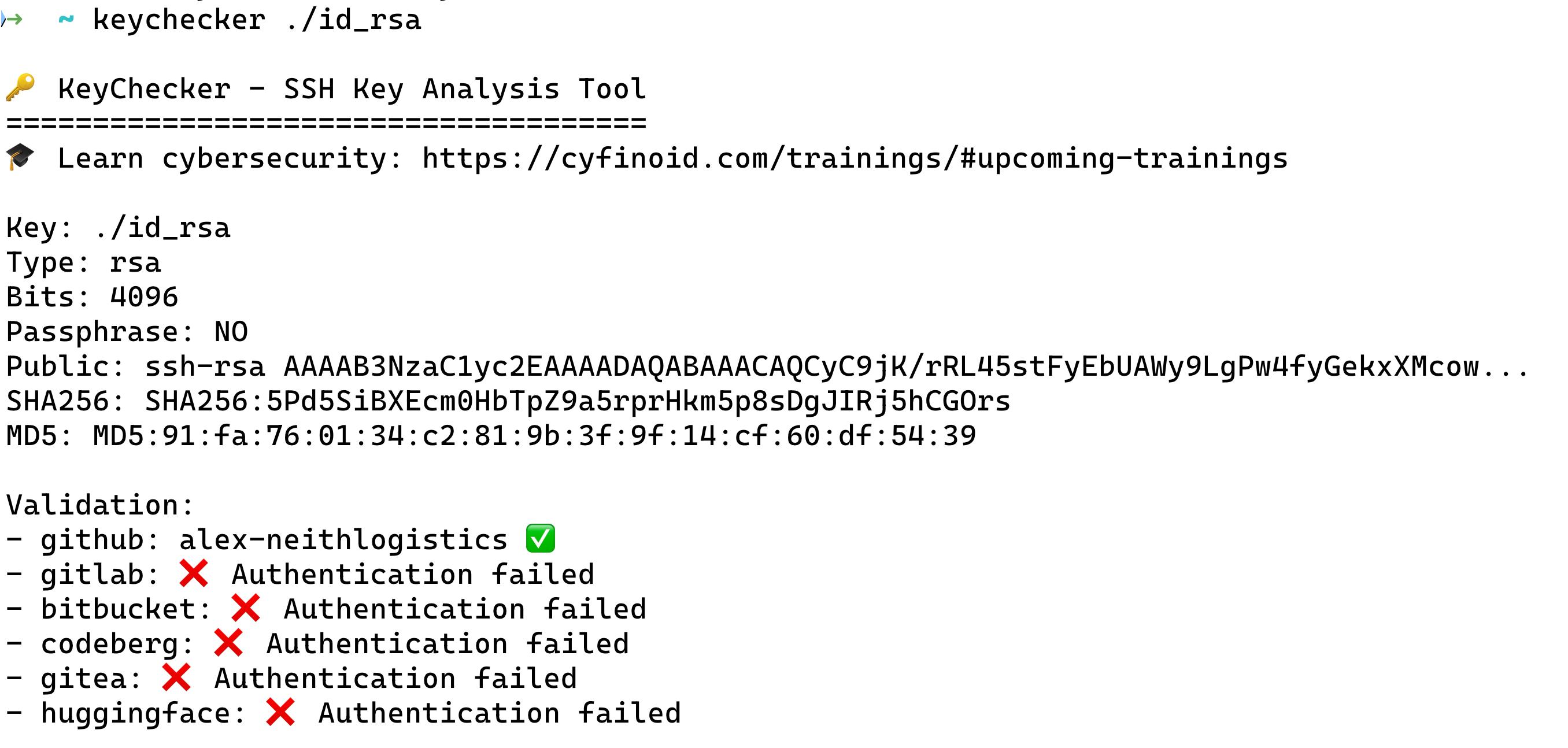
🔑 Fast CLI to fingerprint SSH private keys and identify which Git hosting accounts they unlock.
KeyChecker analyzes a private key locally and validates it against popular Git hosting services to recover mapped usernames, detect weak keys, and optionally probe for private repositories with a wordlist. Everything runs on your machine.
Links
| Categories : |
Software Supply Chain Security
|
|---|

🌐 Mapping the Fediverse, one handle at a time.
Fediverse OSINT is a lightweight tool to collect publicly accessible metadata from Fediverse platforms like Mastodon, Misskey, and more. Whether you’re tracking mentions, discovering linked accounts, or mapping user behavior — this tool helps you gather intelligence with minimal footprint.
With Fediverse OSINT, you can:
✅ Perform OSINT on any known handle across Mastodon, Pleroma, Misskey, etc.
✅ Extract profile metadata (bio, links, tags, followers/following)
✅ Analyze public post content for keywords, hashtags, domains, or mentions
✅ Identify cross-platform behavior through linked URLs and common identifiers
✅ Leverage federation protocols to track visibility and reach
✅ Get results in a format that’s human-readable or export-friendly
Why it works well for open source intelligence:
🔍 Focused on public-facing data only — no scraping or unauthorized access
📡 Lightweight Python script with clear CLI usage
📦 No dependencies on API tokens (where possible)
💡 Great for journalists, researchers, threat intel analysts, and curiosity-driven hackers
Source Code: https://github.com/cyfinoid/fediverse_osint
The Fediverse is growing fast. So is the need to understand how public discourse flows across decentralized networks. This tool gives you a head start.
| Categories : |
Fediverse
|
|---|

🕵️♂️ Discover who a domain really talks to — with zero data leaving your browser.
3ptracer is a browser-first, privacy-focused reconnaissance tool that gives you deep visibility into third-party services used by any domain.
With 3ptracer, you can:
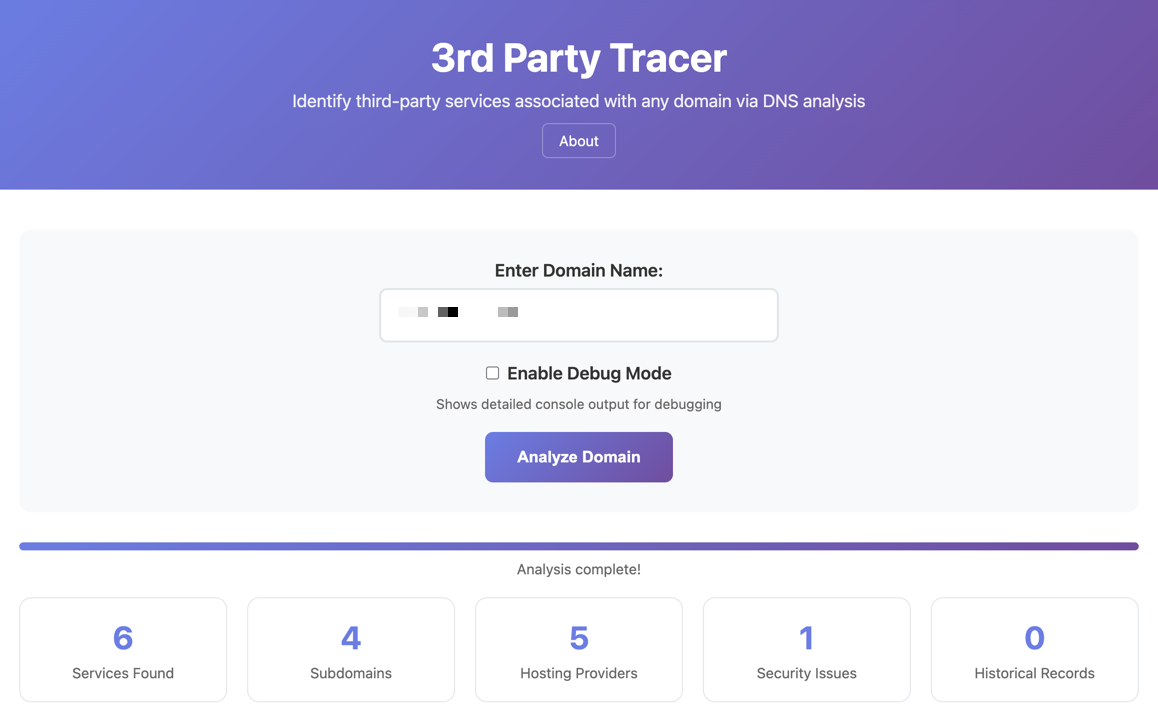
✅ Run comprehensive DNS analysis: Perform live DoH queries and fetch multiple record types (A, AAAA, MX, NS, TXT, CNAME)
✅ Dig into Certificate Transparency logs: Identify shadow subdomains and historical usage
✅ Detect service providers: Automatically spot CDNs, DNS providers, cloud hosting, email services, and security solutions
✅ Analyze security posture: Check for misconfigured DMARC/SPF/DMKIM, and general risk indicators
✅ Visualize the web of dependencies: Get CNAME mappings, service categories, subdomain discovery stats, and historical patterns
Why it stands out:
🧠 Works fully in the browser
🔐 No data leaves your machine
📡 Real-time DNS resolution and fingerprinting
🖥️ No API keys, no shared rate limits
🌐 Built for OSINT investigators, security teams, and curious developers
Check it out: https://cyfinoid.github.io/3ptracer/
Source Code: https://github.com/cyfinoid/3ptracer
This is just the beginning. Explore it, break it, and tell us what you’d like to see next.
| Categories : |
Cloud, Software Supply Chain Security
|
|---|

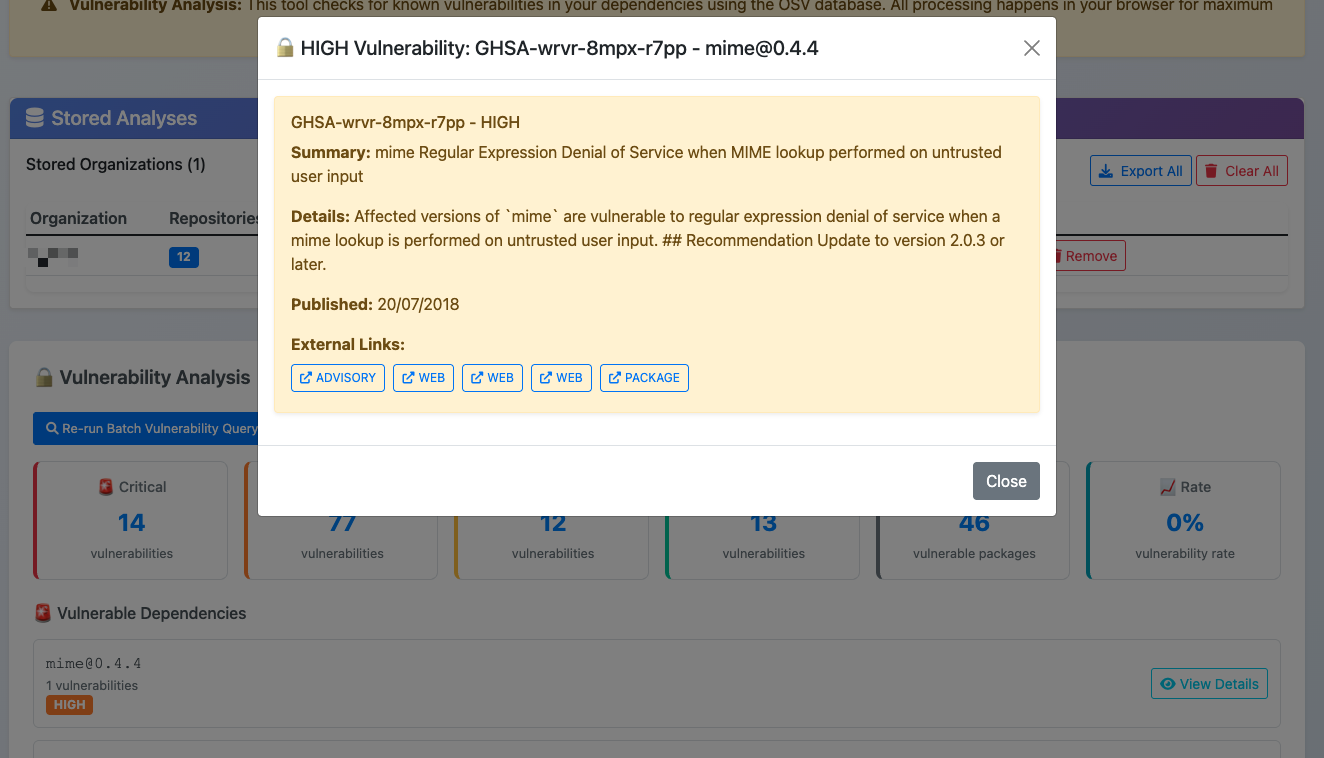
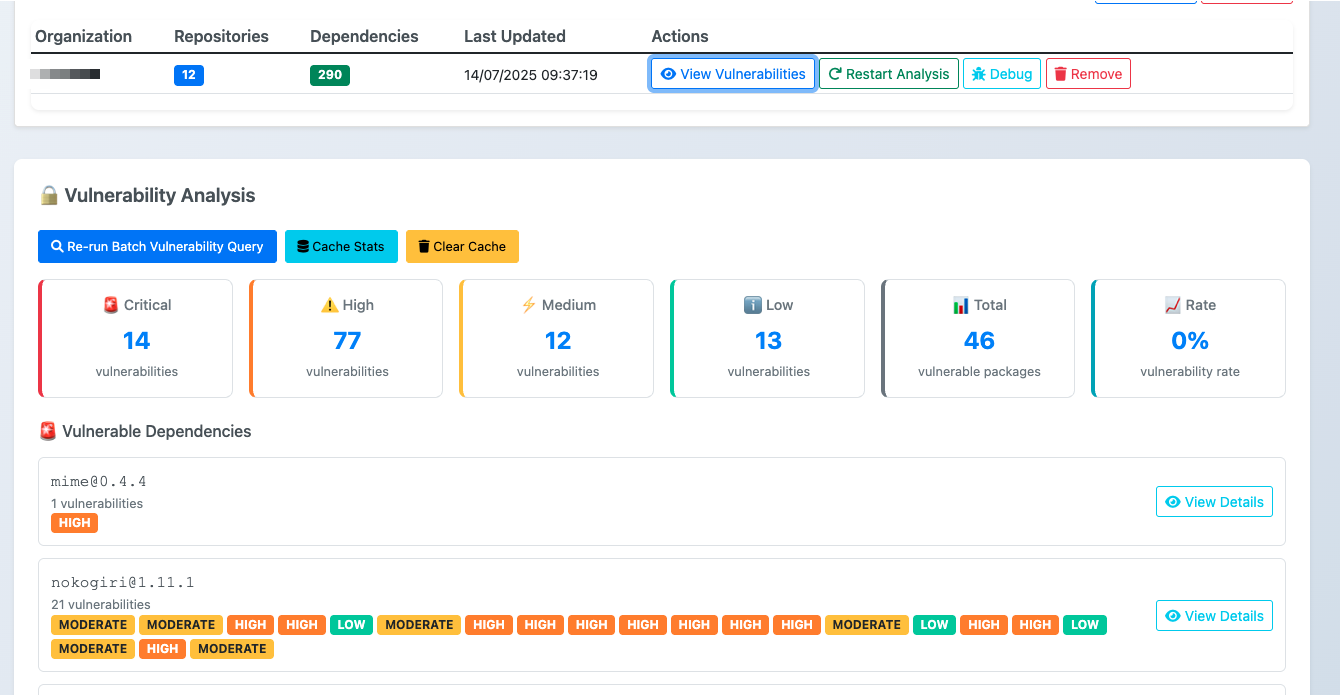
🚀 Introducing SBOM Play – your privacy-conscious SBOM explorer!
🔍 A lightweight, browser-based SBOM viewer that adds vulnerability insights, license analysis, and cross-repo visibility—all while keeping your data private.
With SBOM Play, you can:
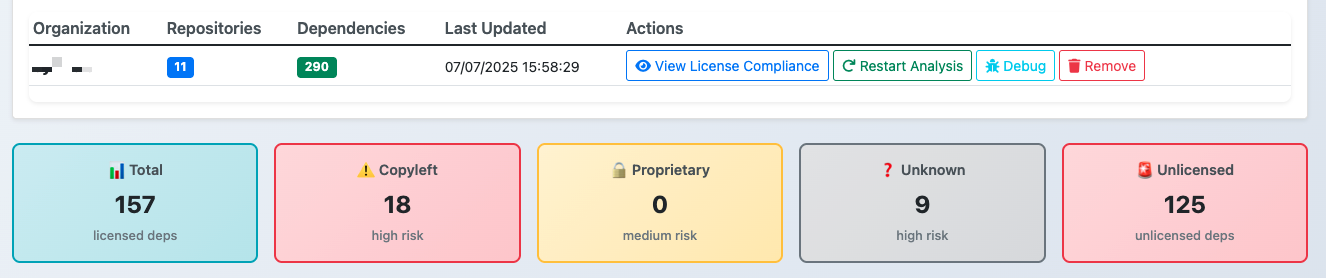
✅ Visualize third-party dependencies across all your repositories
✅ Identify heavily reused dependencies (major/minor breakdown)
✅ Flag missing or incompatible licenses in your dependencies
✅ Get similar insights about your vendors’ dependencies
✅ Understand which components are most affected by known vulnerabilities
✅ Even compare these patterns across multiple organizations if you work with federated SBOMs
🧠 Bonus: It runs fully in the browser
🖥️ No server setup
🔐 No data leaves your machine
📦 LocalStorage for session data
🔍 Fully open source (inspect, fork, or self-host)
Check it out: https://cyfinoid.github.io/sbomplay/
Source Code : https://github.com/cyfinoid/sbomplay
We’re just getting started. Try it out and let us know what features you want next.
| Categories : |
Software Supply Chain Security
|
|---|
Internship Project
Author: Vansh Bulani
The Fediverse is a collection of interconnected yet independent social networks that can communicate seamlessly using open protocols. Users on one platform can follow, interact with, and receive updates from users on entirely different platforms – all while staying within their preferred service. Most Fediverse platforms are free and open-source, fostering transparency and community-driven development.
Thanks to these open protocols, a wealth of data is publicly accessible through the right APIs. This project leverages that openness to collect and analyze various statistics across the Fediverse, providing deeper insights into its scale, activity, and growth.
Project Link: https://github.com/cyfinoid/fediverse-monitoring
| Categories : |
Fediverse, Intern-project
|
|---|

🧠 Simulate a council of AI personas. Multi-perspective reasoning — now in your browser.
AI Bot Council is a browser-based experiment in collaborative AI thinking. Instead of relying on a single chatbot, you assemble a council of AI personas — each with distinct roles, motivations, and viewpoints — to reason through problems from different angles.
Whether you’re trying to explore strategy, debate ethics, or simulate a group decision-making process, AI Bot Council gives you a new lens for conversation.
With AI Bot Council, you can:
✅ Create multi-bot chat environments (e.g., boardroom, courtroom, therapy, hacker meetups)
✅ Assign unique personas, values, and roles to each bot
✅ Simulate realistic interaction patterns: interruptions, side-taking, consensus building
✅ Run structured scenarios with built-in templates or build your own custom setups
✅ Stay in control: human user plays a defined role (moderator, participant, outsider)
✅ Do all of this without leaving the browser
Privacy-first design:
🧠 Fully browser-based
📱 Designed for experimentation and lightweight simulations
Check it out: https://aibotcouncil.anantshri.info/
This is a work in progress — the source code isn’t public yet, but we’re open to collaboration ideas. If you’re exploring group cognition, prompt engineering, or AI behavior modeling, we’d love to hear from you.
| Categories : |
A.I.
|
|---|
Internship Project
Author: Vansh Bulani
This Android APK analysis tool is a fast, modular, and extensible platform designed to bridge the long-standing gap between speed and depth in mobile application security analysis. Unlike traditional tools like Pithus that often suffer from high processing times and rigid workflows, our solution allows users to selectively run open-source tools in parallel, significantly reducing analysis time. Built on a containerized architecture, each analysis component runs independently in Docker, enabling seamless scalability and CI/CD integration. Results are unified and indexed using ElasticSearch, allowing for rapid, structured querying across diverse tool outputs. The platform is purpose-built for developers, researchers, and security professionals who need actionable insights – fast.
Blog Post (ext): Not Your Average APK Analyzer – How I Built a Tool for Deep Insights
Project Link: https://github.com/cyfinoid/apk-analysis-automation
| Categories : |
Android, Intern-project
|
|---|
Internship Project
Author: Johnny Antony Puthur
This project contains an intentionally Vulnerable Android Application. This project serves as a valuable resource for individuals seeking to enhance their understanding of mobile application security. By providing a hands-on environment to explore and comprehend various vulnerabilities, this project facilitates practical learning in an interactive manner.
Participants can leverage this platform to identify common security weaknesses, develop effective mitigation strategies, and ultimately contribute to the advancement of secure mobile application development practices. Through deliberate exposure to vulnerabilities, individuals can refine their skills, stay abreast of emerging threats, and play a pivotal role in fortifying the mobile application landscape.
Project Link: https://github.com/cyfinoid/CFYVuln-android
| Categories : |
Android, Intern-project
|
|---|
Want to know how our interns build and release tools? → Read about our Internship Program